What exactly is SSL? What kind of fraud is it trying to prevent? How does it make you feel secure in the world’s most crowded place — the Internet? Read on for a real-life analogy.
What fraud does SSL try to prevent?
The subtle conman: Imagine that you are standing in a queue to buy a train ticket. 10 minutes later the headcount ahead of you shows no sign of reducing. A nice gentleman poses as an agent from the ticket counter. He claims to speed up the ticketing process for the people who are way back in the queue. If you could give him the fare, he would give you a ticket from the counter.
And he melts away: One of the following two things may happen. You realise that this is a conman and try to alert the authorities. But before anything can be done, the man slips away and melts into the crowd. Another possibility is that you give him the money and he runs away with it. Here too, you alert the authorities, but the man melts into the crowd. Before anything can be done by the authorities, the man is nowhere to be seen.
The boon and bane of a crowded place: A crowded area feels safe. If someone attempts a bold crime, there are others to protect you. But a crowded area can also be a bane, useful for subtle conmen to be active. Beware of the type who look for soft targets, do something stealthy before anyone realises and melt away.
The Internet is no stranger to such subtle conmen. And let’s face it, there is no authority or hierarchy on the Internet. It is up to the local authorities to protect users from international cons, which is a tall order.
Enter Secure Socket Layer
The engineers of the Internet have thus come up with various ways to protect the users. One popular method is the SSL or the Secure Socket Layer.
Authenticity: SSL verifies the service provider’s identity, i.e. it lets the users know that the provider is exactly who they claim to be.
Encryption: Once the identity is verified, all the communication is encrypted such that no one trying to eavesdrop can understand what is being said.
SSL is used in every Internet service we use today, even email and chat. But its most popular and widespread use is to protect the Internet’s most common user, the web surfer. You have heard this security method’s name several times — HTTPS or HTTP secure.
Components of SSL
There are several participants and components in the SSL narrative. Here, I will introduce you to them in the form of a cast. We shall then see the SSL process as a short story.
The user: Sid
Meet our Internet savvy user. 20-year old Sid loves to purchase things online. This is who we are trying to protect so that the Internet conmen do not steal his money. Sid uses a browser like Google Chrome, Firefox or Safari.
GoodProducts.in
This is our story’s fictitious e-Shopping website where Sid buys his favourite products. They facilitate payment using the payment gateway MyRupeePurse.in.
MyRupeePurse.in
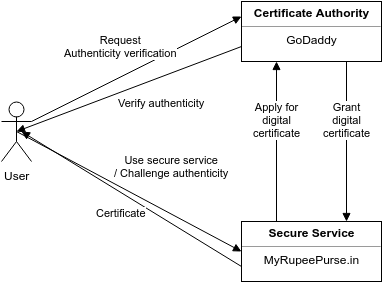
MyRupeePurse is our fictitious payment gateway service which Sid often uses to pay for the goods. MyRupeePurse.in has enabled SSL using GoDaddy so that,
- Authenticity: Purchasers like Sid know that they are using the legitimate MyRupeePurse.in and not an imposter. SSL enables a service to hold a certificate of authenticity.
- Encryption: All communication between Sid and MyRupeePurse.in is secure, using a method called private-public key pair, which we shall see shortly.
GoDaddy
GoDaddy sells domain names such as MyRupeePurse.in. But importantly, they also sell digital signatures. We will soon see what digital signatures are.
Sid and his web browser completely trust GoDaddy. That makes them a Certificate Authority.
SSL certificate
Every individual can be authentically identified by his/her passport. Additionally, Indians can be identified by their Aadhar number and Americans by their social security number.
SSL certificate is similar. It serves as a valid, certified ID for a service provider, such as MyRupeePurse.in. The company applied for their certificate from GoDaddy.
Unfortunately, passports have been heavily faked. SSL certificates can be too. But fake certificates will be caught as we shall see later.
Digital Signature
When a certificate authority authorises an SSL certificate as belonging to a service provider, they also leave their own signature on that certificate. Since the authority themselves are trusted by the user, their signature helps a user trust the service provider too. E.g. Because GoDaddy signed over the MyRupeePurse.in, Sid trusts them. GoDaddy thus vouches for the authenticity of MyRupeePurse.in.
There are trustworthy ways to verify that a certificate was indeed signed by a certificate authority like GoDaddy. This helps prevent online fraud.
Private key / public key pair
Magic lock with two keys: Let us think of a special box with a magic lock. This magic lock has two keys and exhibits a peculiar behaviour. Let us call them Key 1 and Key 2. If the lock has been locked with Key 1, then it can be reopened only with Key 2 and vice-versa. Wizard Taalakam Guru (‘master of locks’ in Sanskrit language!) is in charge of the box, the lock and the two keys. This can potentially create powerful security.
Private and public keys: The wizard wants a reliable way for people to be able to send him messages in the box, such that no one else can snoop. If someone requests that he/she wants to send the wizard a protected message, the wizard makes a copy of Key 2 for use by that person. The box, the lock and the copy of Key 2 are sent to that person. The wizard protects Key 1 with all his life and will not hand it over to anyone under any circumstances.
Protected communication: The messenger writes the secret message, puts it into the box and locks it firmly using Key 2. He/she can rest assured that only Key 1 and hence only the wizard can open the box. The wizard, having read the message, composes his reply, puts it into the box and locks it with Key 1 and can safely assume that only those with a copy of Key 2 can open the box.
Key 2 can be distributed in copies to the people who want to maintain a secure communication with the wizard. Key 2 is the public key. However, Key 1 MUST be guarded by the wizard at all costs. Its compromise will break the entire security. Key 1 is the private key.
The SSL screenplay
Now that we have seen all the components and roles of the SSL screencast, let us go through a few stories.
Digital Signature Application by MyRupeePurse.in
Cast: MyRupeePurse.in, GoDaddy
MyRupeePurse.in to GoDaddy: Listen, I want to make my website secure. As requested by you, I have filled up an application form (CSR or Certificate Signing Request) for a certificate that I would like to present to people who want to pay through our service. Can you help me get a digital certificate?
GoDaddy to MyRupeePurse.in: Sure, I see that no one else has applied for a certificate with this domain name, so you are eligible. Please just hand me your application form, please. I’ll give you a signed certificate.
GoDaddy creates a signed certificate, with its signature at the designated place. But then it does something cool. It sticks a small box on top of the signature and locks it with a magic lock designed by our wizard, using a private key that only they possess. Then they put their seal on top of the box.
GoDaddy to MyRupeePurse.in: Here you go. Remember, you can never open this box. But don’t worry, if anyone asks to see this signature, we will help them open this box. If you remove this box and display the signature in plain sight, we will consider this certificate as tampered. Keep that in mind. All the best.
Now MyRupeePurse.in can rest assured that only they are in possession of GoDaddy’s authorised signature to host on the particular domain named MyRupeePurse.in. No other party can claim that domain. It is time for them to rock the show.
Now we trace through Sid’s purchase story to see how this entire thing works.
Sid’s purchase and payment
Sid to GoodProducts.in: Okay, I love these shoes and would like to checkout and pay? Please guide me.
GoodProducts.in to Sid: Sure, we take all our payments via MyRupeePurse.in. Let us guide you there. Once you complete your payment, we will know and shall let you have these shoes. Thanks for your shopping, sir.
Sid to MyRupeePurse.in: Listen, GoodProducts.in sent me here to pay for my order with them. But first, I would like to verify that you are indeed MyRupeePurse.in and not an imposter.
MyRupeePurse.in to Sid: Sure, I have my SSL certificate. You can have a look.
At this point, the certificate may have no digital signature at all. Or the signature may be visible in plain sight without being protected by the box with the magic lock. Sid can shout out, “Hey, this is fudged! Imposter! Thief!!”
However, let us assume that it is an honest start.
Sid to MyRupeePurse.in: Hmm, okay, I see a seal of GoDaddy on this box. Let me go to GoDaddy to find out if this signature is real and if your certificate is so too.
Sid to GoDaddy: Listen, I have got this person claiming to be MyRupeePurse.in and I have been given an SSL certificate affixed with a digital signature. The signature is protected by a box which has your seal. Do you know any MyRupeePurse.in?
If GoDaddy says, “I have no idea who that is!”, then Sid can yell “Thief!” again.
But in a happy story,
GoDaddy to Sid: Yup, we do know MyRupeePurse.in and we did give them the authority to set up an SSL-enabled service over that domain name. You say you see a box with our seal. Great! Let us help you open it.
GoDaddy makes a copy of the public key corresponding to the private key with which they locked the signature box.
GoDaddy to Sid: Okay, here is a key that should help you open this box. If it is indeed our signature, this key can open the box. If this key is unable to open the box, then the signature and the box with our seal have been faked.
If Sid is unable to open the box, he is within his rights to yell again. But fortunately, the certificate is valid.
Sid to GoDaddy: I can open it. Thanks, GoDaddy. I will go back to MyRupeePurse.in now. I know they can be trusted.
Sid to MyRupeePurse.in: Alright, MyRupeePurse.in, I have verified that you are indeed the correct party, let us go ahead with this payment.
MyRupeePurse.in to Sid: Cool Sid. Okay, now let us proceed. But I want to make sure that no one mishandles the money from your credit card. Since this is a remote transaction, I cannot physically handle your card to use a swiping machine. I need your card’s number and CVV. I don’t want anyone to intercept those details along the way. Let’s go secure.
I will give you a form with blanks to be filled in, mostly your credit card details. The form is to be enclosed in a box that has a lock. The lock can only be opened by a key that belongs to me. Here is another key that you can use to secure the lock. Once you fill the form, please put it in the box, lock the box and send it to me.
The security is ensured by the private-public key pair belonging to MyRupeePurse.in. After the payment is done, MyRupeePurse.in leads Sid back to GoodProducts.in with a payment acknowledgement.
GoodProducts.in to Sid: Your payment via MyRupeePurse.in was successful. Enjoy your shoes. Thanks again for shopping. Here is your receipt.
Conclusion
In the above story, you saw how MyRupeePurse.in and GoDaddy have set up a fraud-free environment for Sid to shop without worrying about losing his money to conmen. Many people, typically seniors in small towns with recently acquired knowledge about technology, are still apprehensive about shopping online. But the above story hopefully clarifies how safe it is.
Does your company provide SSL-based services to your clients? Do you specifically point your browser to the HTTPS-enabled version of websites? Do you consciously verify that your preferred bank, email service and chat service take you to HTTPS and SSL based URLs? How safe do you feel while accessing your information over the Internet? Please let me know about your experience in the comments.
Further reading
- Other blogs
- Article on Medium: 4 Reasons Why An SSL Certificate Is Important For Your Company Website
- Article on Medium: The importance of SSL and HTTPS in web security


That’s a cool story explanation !! Now I understand atleast a little bit on what Whatsapp’s encryption is all about and Mark Zuckerberg’s account been snooped.