You have just moved your desired product to the shopping cart of your favourite online shopping website. The website asks for your preferred mode of payment. You enter the details of your bank/card and click to proceed. Just before your payment is complete, you have one more step to complete. On the screen in front of you is a text box which expects 4 digits. But where do you get those 4 digits from? That’s when your phone pings. You reveal the source of the ping to be an SMS that contains 4 digits. The same digits that you need to enter on the screen to complete your payment. With the magic digits entered, your payment is unlocked and your product will soon be on its way.
Welcome to the world of OATH or Open AuTHentication, a specification that uses two steps of authentication to make sure that your transactions are truly safe. Let’s read how OATH works.
No relation to ‘OAuth’
Please note that OATH is not to be confused with OAuth. OAuth with a ‘u’ in the middle is a way to give a certain software B only as much access as it needs to access your data in software service A, without giving service B your username and password. E.g. Instagram only gets to post photos on your Facebook timeline. It cannot modify your name or date of birth. Nor does Instagram know the username and password to your Facebook account. Facebook gives limited access on your profile to Instagram.
The goal of OAuth is authorisation and not authentication. OAuth assumes that the person is already authenticated, i.e. you have already logged into a service and identified yourself. Once you have logged in, OAuth determines how much access is to be given. Which means, OATH with no ‘u’ and a capital ‘T’ and ‘H’ occurs a step before OAuth. OATH is the nuts-and-bolts for the authentication process, i.e. the step where you identify yourself.
A good one-liner mnemonic to not get confused between OAuth and OATH is:
OAuth starts when 'u' are added by OATH.
In other words, before OATH, you are unknown to the system. Once OATH does it’s magic, the system knows about you. So now OAuth can take over.
Basic principle of OATH
OATH’s authentication process requires you to identify yourself in two steps. The two steps attempt to answer the following question.
- What is your IDENTITY?
- WHO are you?
- What do you KNOW that others don’t
- What do you uniquely POSSESS that proves it’s actually you.
This two step authentication is often called two-factor authentication and is shortened as 2fa.
A non-software example

Here is how you may do a two-step authentication when someone knocks on your door.
Knock, knock!
Identity steps
You: Who’s there?
Other end: Aakash
You: Really? Do you remember that last year we went for an interview together. Which company was it, when and where?
Other end: It was Tech Mahindra in Navi Mumbai on June 3rd, 2017.
Proof step
You: That’s right. but you could just happen to know Aakash’s name and his interview details. Aakash always carries some Mentos in his pocket. Can you slip me one down the post slot of my door for me to see? Then, I will open the door.
What is your IDENTITY?
In the old days of authentication, this first step was enough. Let’s divide this step into two sub-steps. The first sub-step asks for your identity and the second sub-step looks for something that only you know and have not shared with others.
The first sub-step may be your username, mobile number, credit card number, Aadhar number, PAN number, demat account number or anything that is unique to you. In our door example, the person on the other end uses the name ‘Aakash’.
The second sub-step is to ensure that the person is really who he/she claims to be. In our door example, the person on the other end is asked about an interview that he attended with you. Such level of detail is possibly known only to the person who really attended the interview. Others will forget such fine details. In the software example, we have passwords, card CVVs, hint questions and PIN numbers for ATMs. It is based on the trust that you will not share such sensitive information with others.
It wasn’t enough
We are in an era where identify theft is easier than before. Cards are stolen, usernames and passwords are phished, ATM machines are rigged and company databases are routinely hacked. Plenty of times, these are companies with big brands and commendable track records. Internet has levelled the playing field and the identity-and-secret method is not sufficient anymore.
What do you possess that others don’t?
To defeat the problem of identity theft, several companies joined hands and came up with OATH specification that still uses identity as the first part of authentication. But then, they added another step. You need to possess something physical and unique on you. Something that is part of you. Something that is in your possession that you don’t share. Or if you share, you do so with an eye on it. Even if your identity is stolen or is used without your consent, the intruder will still need that thing in your possession.
When the person claiming to be Aakash came to your door, you remembered that Aakash has a habit of consuming Mentos and always has one with him. Even if someone were to get Aakash’s identity information and a history of his interviews, a small habit such as Mentos addiction is probably overlooked and an intruder won’t have Mentos to slip through your door’s mail slot. If a packet of Mentos does plop to the floor from the slot, then you can be reasonably sure that the person on the other end is indeed Aakash.
Here are some options that are used in the world of technology in the order of strongest security to the weakest.
Biometrics: These are the strongest and the most unique personal possessions. Biometrics are impossible to lose to theft since they are the part of you. They are very difficult and expensive to copy / duplicate. Fingerprints and iris scans are the most secure ones, followed by facial and voice recognition. Other features like recognition of foot impressions are being developed for the future. Since smartphones have fingerprint readers these days and fingerprint scanners are available for cheap, this feature is the most commonly used biometric for two-factor authentication’s second step. In fact, with the use of biometrics, most services simply forgo step 1 of identification (what you know), since the biometrics are unique and good enough to identify you in one step. But some biometric companies have paranoid level safety, e.g. military or the central government premises and will often ask you for a password even after having identified you correctly from your biometrics, just in case someone with really high connections is uses advanced technology such as fingerprint duplicating.
India’s payment through Aadhar Pay is one of the best examples of usage of biometrics to ensure the identity of the payer. It makes sure that no transaction happens unauthenticated.
A device with a chip: Many companies hand out smart devices with microchips that are unique per device. In a highly secure system, you are asked to key in your credentials (something you know) and then use the smart chip (something you have) to identify yourself. This step can be also be the other way round. You may be first asked to produced something you have and then asked to key in something you know. Either way, you are identified in two steps. An intruder would need both the possession and secret to gain entry on your behalf.
The best example of such operation is in ATMs, where you are to insert the card (something you possess) in the machine’s slot, but then also key in your PIN (something you know). Losing both to the same time to an intruder is often unlikely.
One time password (OTP): After the initial entry of credentials (something you know), a one-time password, valid for only a length of time (e.g. 30 minutes), is sent to something you possess. This is usually an SMS to your mobile phone or a link to your email. Email is not a physical possession as strictly required by the second step of OATH, but it is still unique and personal enough. Plus it gives the flexibility of access from any connected place with a computer.
The OTP method is good in the sense that almost everyone has a mobile phone or email. However, both are routinely handed to several persons such as relatives or friends. The OTP method is painfully prone to backstabbing by someone close to you if you let your guard down.
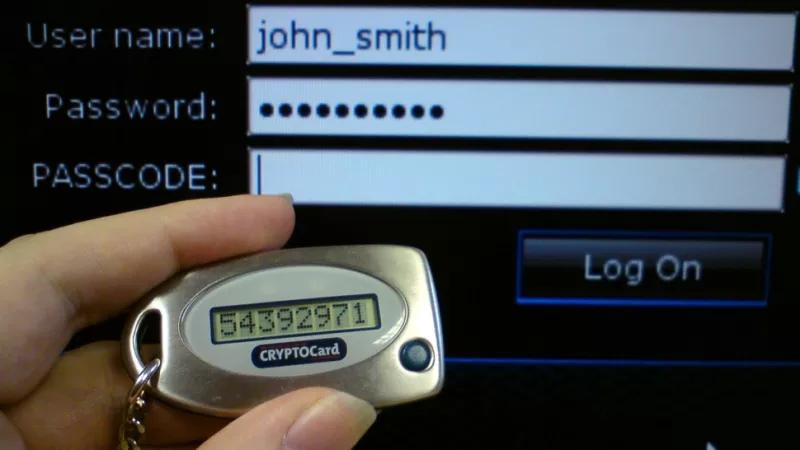
This has made certain companies, such as those which produce stock trading software, come up with a unique OTP generating device for their customers. This device displays the OTP that is to be keyed in to the software to authenticate an investor and to authorise the transaction. The OTP changes rapidly with time, a new OTP showing up on the device every 30 seconds.
Conclusion
The world of security keeps changing everyday. New technology frequently replaces old ones deemed either outdated or easily hackable with updated technology from the hackers too. But the principles of security never change. OATH is a specification that sticks to principles, i.e. three questions over two stages, without dictating what technology is used. So long as the three questions are answered to the satisfaction of that technology, the system is secure.
Here is my exercise to you. Look around you and find software and non-software systems that you would want to apply OATH security to. How can the three questions be answered for that system?
